If like me, you are tired of having your screen cluttered full of stupid ads, c/w the general enshittification of the Internet by commercial interests, then you may wish to try /etc/hosts file “hostile server blocking”. It’s free and no additional software is needed. This is because your /etc/hosts file part of your computer’s TCP/IP stack. This method will rid you over 99% of third-party served ads, along with a gamut of other internet nastiness. Even better, this method protects your entire machine from ads and other junk, not just one specific browser. Chrome, Firefox, Konqueror, Opera – I can’t see a single ad. Not even a small one. 🤣
Regular readers will know I’m a long-term GNU/Linux user, with a particular dislike for those that force content onto my computer that I have not specifically requested. However this technique works on any OS that uses a standard TCP/IP stack, providing you have the necessary access permissions. I will describe how one does this on a Unix-like operating system, such as Debian, Ubuntu and any of its many derivatives. I will discuss other OS’s later in this article with appropriate links.
First, find a good, regularly-updated block list
This is currently one of my favourites…
Then find your hosts file
In Unix-like systems such as Debian, Ubuntu and its various derivatives, it lives at /etc/hosts. You if you are in doubt, it’s probably easiest to use your favourite file manager to find it. This is how I normally do it…
Important: make a backup copy of your existing hosts file
Whatever OS you run, you should always make a backup of a configuration file before you edit it. A few seconds spent now can save hours or even days, if you mess it up. Various ways to back up a config file. But on Unix-like systems it is often easiest to do from a terminal window.
sudo cp -v /etc/hosts /etc/hosts-original
returns…
'/etc/hosts' -> '/etc/hosts-original'
Then confirm the file has actually been copied…
ls -la /etc/hosts*
returns something similar to…
-rw-r--r-- 1 root root 5643688 Mar 29 20:58 /etc/hosts
-rw-r--r-- 1 root root 411 Mar 29 18:07 /etc/hosts.allow
-rw-r--r-- 1 root root 711 Mar 29 18:07 /etc/hosts.deny
-rw-r--r-- 1 root root 5643688 Apr 14 23:36 /etc/hosts-original
Editing your hosts file
Firstly open /etc/hosts in a text editor of your choice. Several methods to do this.
Option 1: using a command line editor…
sudo nano /etc/hosts
Option 2: using a GUI editor…
sudo gedit /etc/hosts
Or my preferred method using Kate (KDE Advanced Text editor)
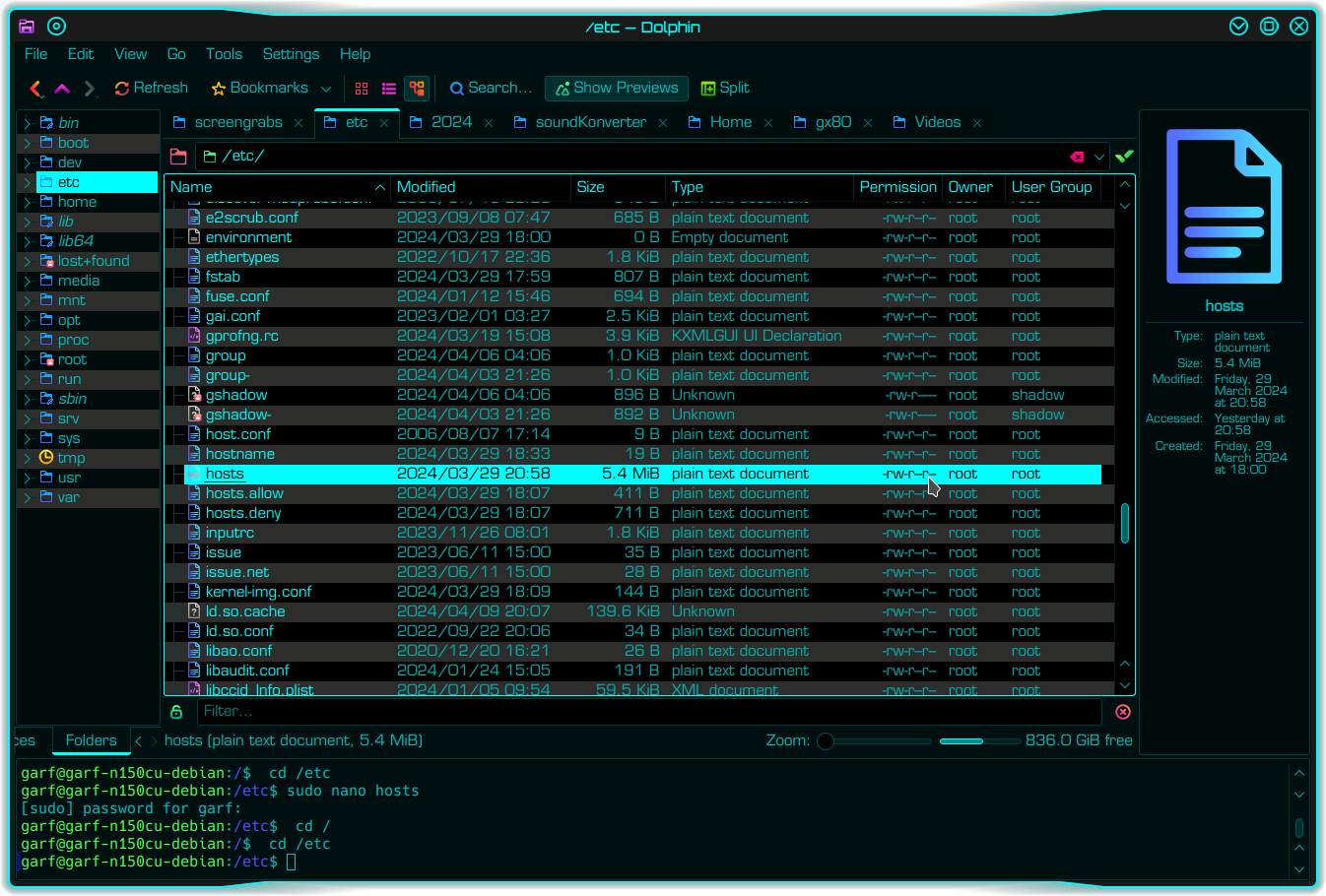
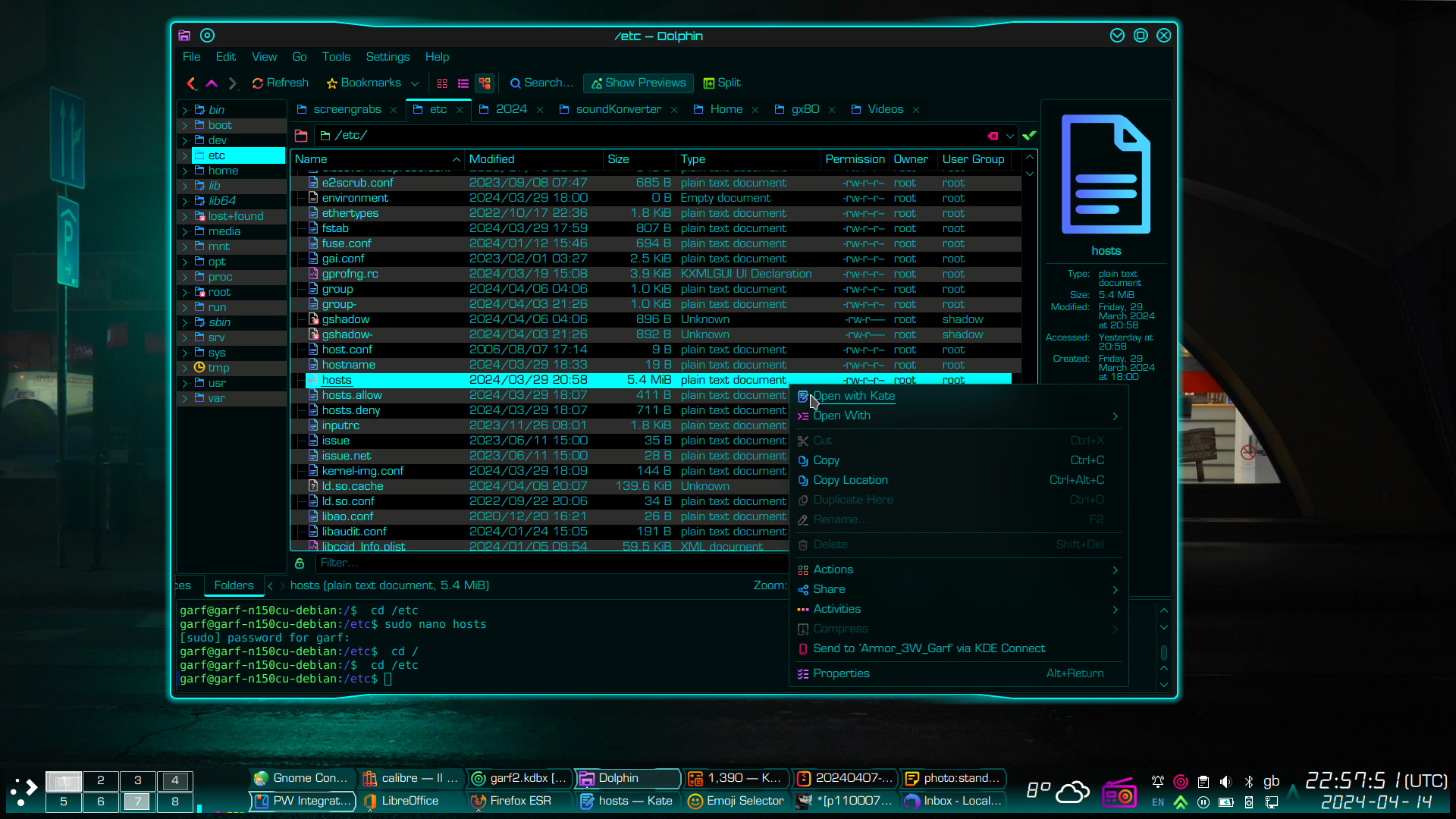
Now Kate is a fabulous text editor. But it cannot (usually) be opened as root. Instead you open it as a normal user, then it automatically seeks root permissions when you try to save a file that requires root write permissions. In systems using KDE desktop, Kate is the default text editor and will open a file directly from the Dolphin file manager, thus…
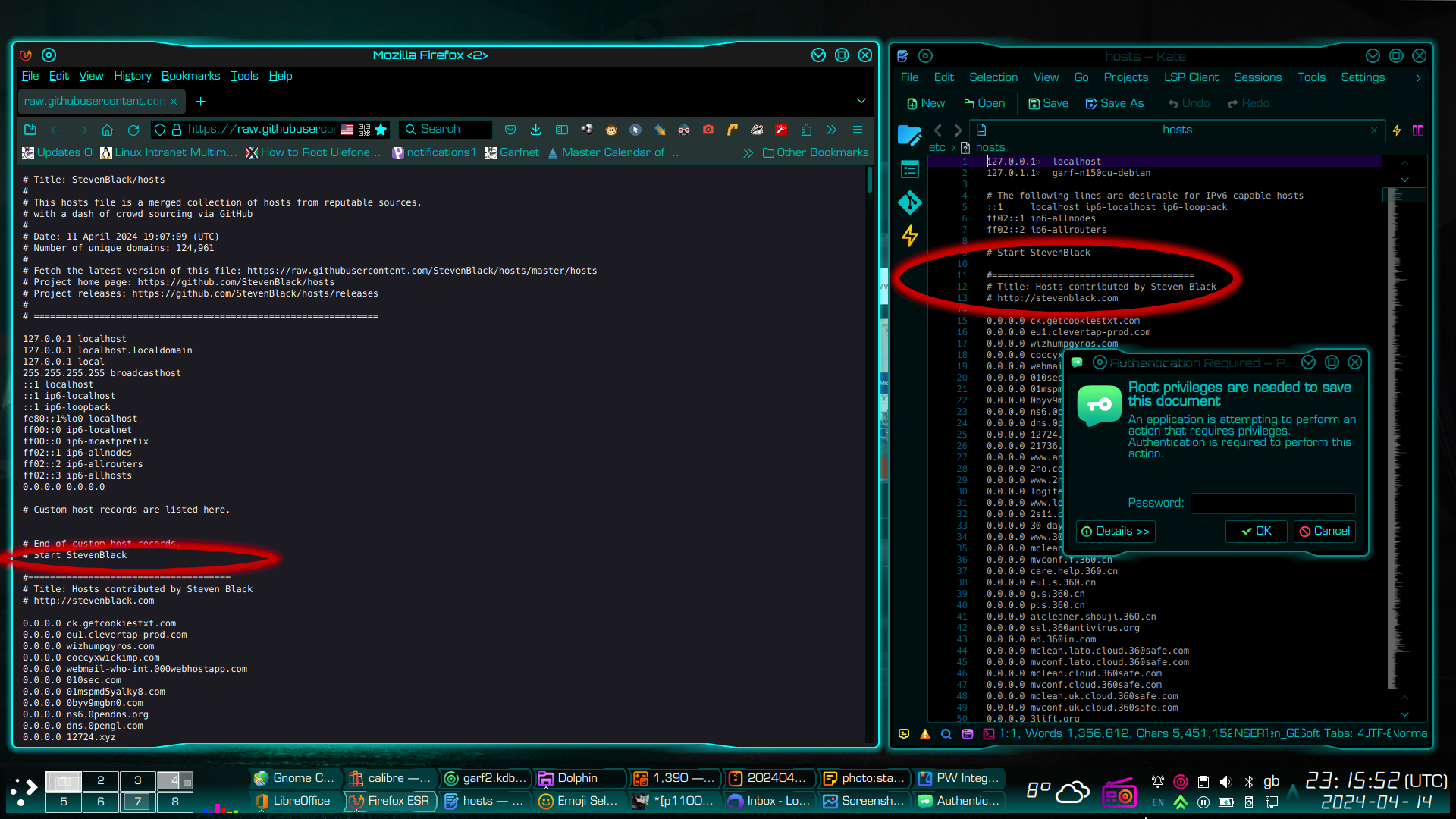
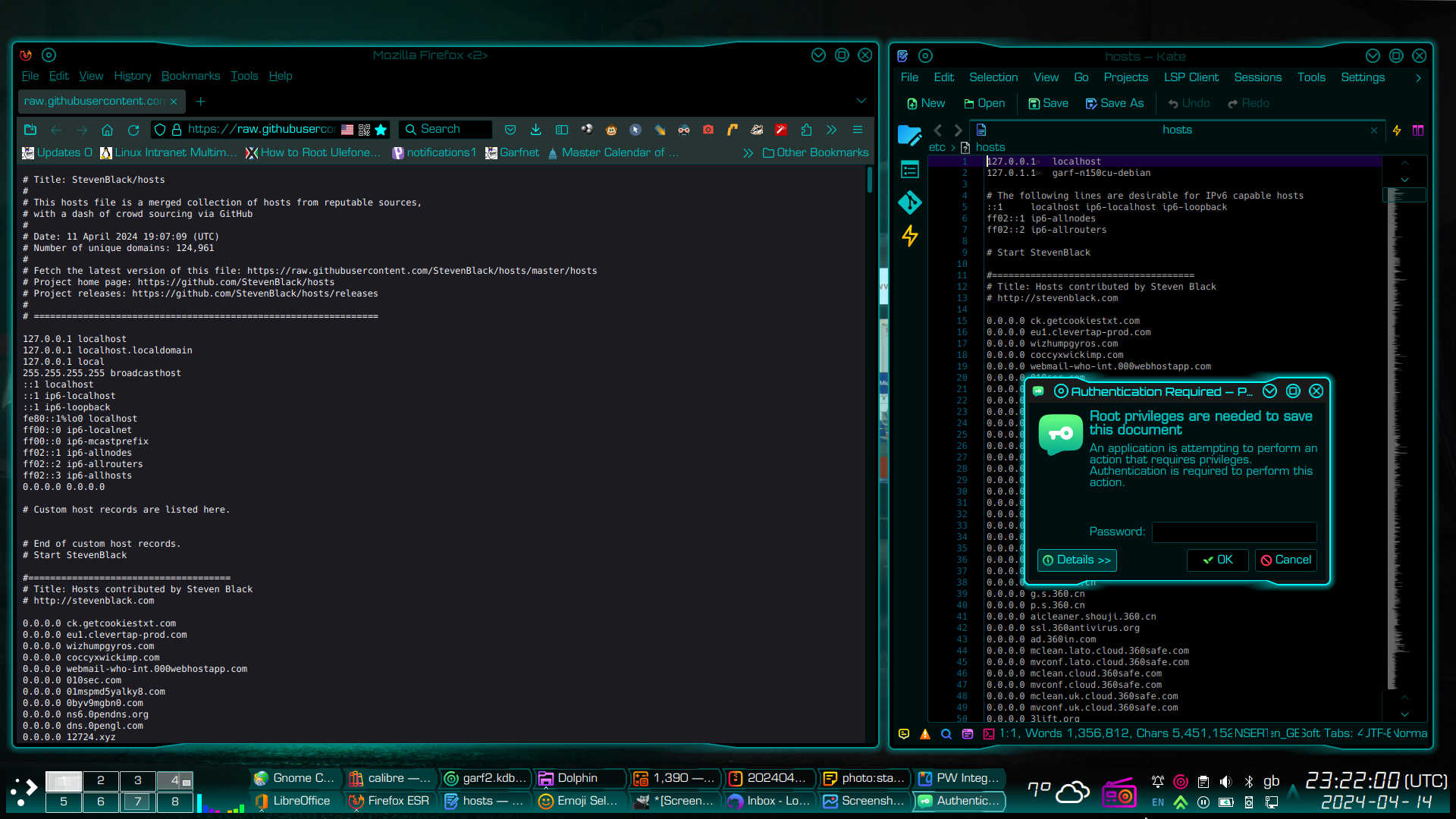
The screenshot below shows Mozilla Firefox browser on the left, viewing a copy of Steven Black’s block list, on-line. The pane on the right is Kate text editor. Simply copy the part of the block list that reads “# Start StevenBlack” and EVERYTHING below it (shown left), and paste into your /etc/hosts file below its default contents (shown right). The top of the relevant text is circled in red, below.
- Note, the text itself is some 180,000 lines long, so it may take a little time to select it all.
- Also note that Kate has an additional feature where it shows a large text file in greeked text down the right hand side, next to the vertical scrollbar, to help you find your way around the file, and will show when you have pasted the blocklist into the file. I have ringed this in blue. Most other text editors do not have this feature.
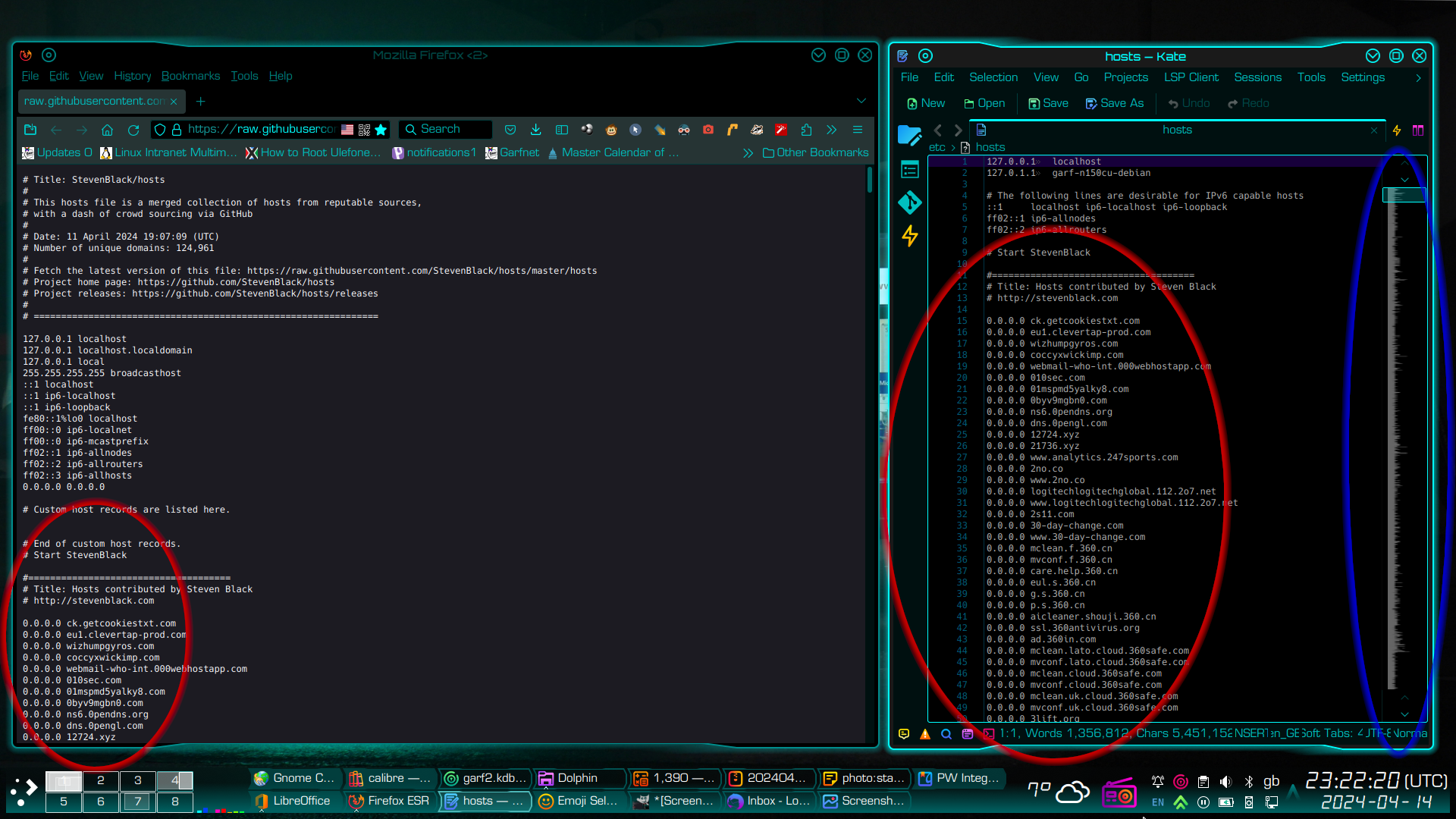
Save your hosts file in the usual way. In Kate, you will be asked for your root password…
Keeping your hosts file updated
You may need to update the file every now and then. Simply open your /etc/hosts file as described above, in a text editor of your choice, select and delete the old entries, and copy and paste the body of a new block list. I do mine at roughly 90 day intervals.
What about Windows users?
Windows users’ hosts file is normally nested some where beneath the C:\Windows\system32 folder. Probably…
C:\Windows\system32\drivers\etc\hosts
In principle, you do the same as you would in Unix-like systems, namely copy and paste a block list into your hosts file, having first made a backup copy of your original hosts file, of course! And just like Unix, you will require the necessary permissions in order to edit your hosts file. Typically, you would need to log in to your Windows computer as “Administrator”. And you would use Windows Notepad as your text editor.
This chap covers the details of actually opening and saving your hosts file on Windows 10 and Windows 11, with significantly more detail than I can provide…
What about mobile computing devices?
If you have an Android phone, and you can figure out how to root it (to get the required access permission), then you can protect that device too, using exactly the same method. On Android devices, the hosts file generally lives at
/system/etc/hosts
Don’t want to go into too much detail here, because you will almost certainly need to root the device first. But those considering rooting their phone might find this an interesting place to start…
Though I would add that using a rooted phone is lovely. In addition to blocking irritating browser ads and pop-ups, it also kills almost all in-app advertising too. Rooting has lots of other benefits because it also gives one root access to its Linux subsystem. Effectively turns your smartphone from being an irritating ad-riddled toy into a seriously powerful handheld computer. Means you can divorce it from Google too, if you wish. 🙂